You’ve heard the analogy before. Your enterprise is a fortress. Protect it with towers. Build stone walls to protect your data. Build a moat to keep the bad guys out.
I assert that this is not the correct mental model for defenders of enterprise networks and applications to have, and security leaders should not be promoting this viewpoint within their organizations.
The problem with this mental model is that thinking of a fortress with its huge stone wall or towers gives the impression that this wall has no holes or vulnerabilities. It implies that nothing from the outside can break through the fortress walls.
It leads to the idea of stopping any and all breaches of that wall. How easy or likely is it to break through a massive stone wall (using the weapons that were common when castles and fortresses of stone were popular)?
If that is true then what happens when someone destroys your wall and breaks in? By the time that happens, you don’t really have much of a chance of fighting off your enemies anyways.
Let’s first take a look at the wall itself.
Is It Really a Stone Wall?
Is your network perimeter best likened to a stone wall around a fortress? Let’s think about it for a second.
A good wall around a fortress allows nothing through. Is that true for your network perimeter? Probably not. In order for business to be conducted and money to be made, certain traffic must be let through.
Is your website very useful without port 80 (HTTP) and port 443 (HTTPS) opened up? Not really. Web Application Firewalls (WAF) are often forced to whitelist certain traffic to allow legacy systems to continue running, even if that traffic would normally be stopped.
The point is, instead of blocking all access to your network, your perimeter allows some traffic to go through. This is done deliberately, with a certain purpose in mind. This traffic is required in order for the business to function.
A more appropriate analogy is a cell, such as a bacterial cell or the trillions of cells that make up the human body.
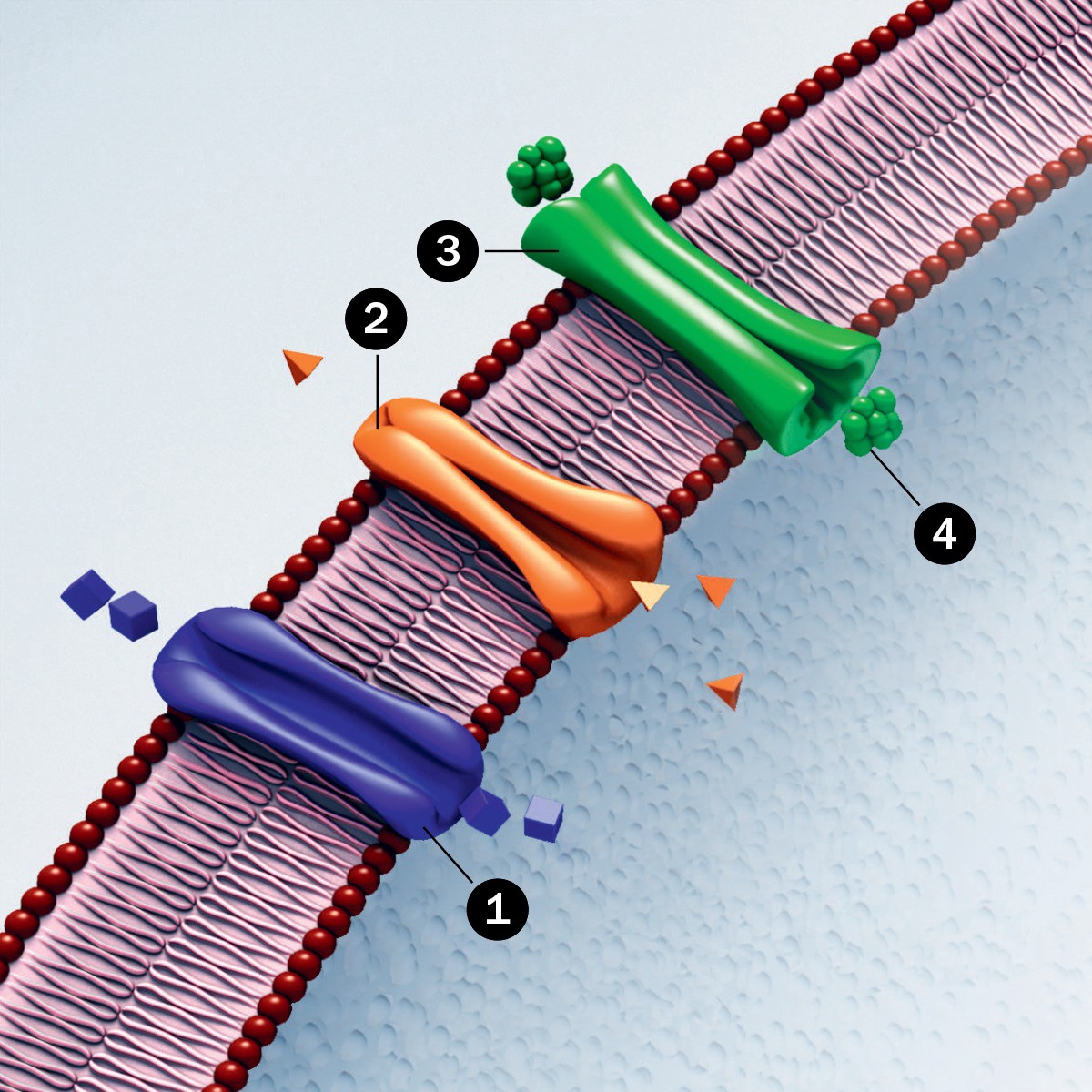
Cell walls protect the cell from the potentially damaging molecules. However, there are special protein molecules embedded in the wall that act as “security guards” and let certain molecules in.Cell walls allow access to the molecules needed for the proper functioning of the cell while keeping unwanted molecules out. This is happening on the surface of even the simplest cells.

A view of a cell wall. This is what your perimeter really looks like. (Source)
This mental model is more realistic for networks. A network that is completely closed off (like a stone wall) would not provide a whole lot of value to the business. Instead, we choose what traffic we allow into the network while keeping unwanted traffic out.
But what happens when something we don’t want does get in?
Building a Network Immune System
When you have a huge wall around your castle or fortress, you feel like you are impregnable. You are safe from the enemy. You may have heard one of these statements before:
-
“We have the latest firewall from Company XYZ. No one can get into our network.”
-
“We a finely tuned WAF. Our applications are safe.”
-
“We’ve never had a breach, so we don’t need to pay that much attention to security.”
This mentality is counterproductive. It can lead to a false sense of security, moving security organizations to feel like they are protected.
Instead, the best way to defend a network is to act like our immune system. It doesn’t assume there are no threats. It knows how to defend the body when threats appear.
Skin and mucus make up the first basic “perimeter” of defense. If a germ gets past those defenses, then the white blood cells kick in to detect and defeat the invaders.
There are three types of white blood cells that protect our bodies from adversaries. One in particular, the lymphocytes, create antibodies that are built to destroy specific threats.
The awesome thing is that the immune system remembers the characteristics of a germ. If that germ ever returns, it can be destroyed immediately. (Source)
Your network and security program should be like the immune system. Don’t sit back to be picked apart by attackers. Don’t be the next breach headline because an attacker stays in your network for 6 months undetected. How do you do this?
Responding to Threats
Incident response has been a staple of cybersecurity for quite some time. This is usually done by automated tools that try to find possible intrusions and create alerts for analysts.
A recent development in this space is a technique called threat hunting. Threat hunting involves analysts “patrolling the territory” to find threats.If there are gaps in what your automated tools are detecting or if adversaries have bypassed them, threat hunting can help to reduce the risk. The general goal of threat hunting is to actively seek out those who have made it past the defenses so that they can be stopped before any real damage is done.
The information gained by threat hunting can then be fed back into the automated systems in order to make them better at finding threats. This creates a positive feedback loop that leads to an advanced threat detection machine within your organization.
When it comes to application security, it is just as important to know when they are being attacked and react to that attack. Runtime Application Self-Protection (RASP is an emerging technology and industry that aims to do just that. It can help eliminate threats at runtime.
A RASP hooks into a running application. It watches the execution of the application and then stops attacks as they are detected. Advanced RASPs can learn the “normal” operation of your application and react to any anomalous behavior. Others watch untrusted input and stop malicious input in its tracks.RASP is not a silver bullet and does not catch everything. However, it can be a valuable defense-in-depth strategy and can help your overall security posture.
For instance, a RASP system can tell you what specific attacks your application is really facing in production. This can help you to prioritize vulnerability fixes based on what is actually happening, not just what might happen.
These types of tools can be a boost to your network “immune system”.
Regular Checkups
Even though we have an immune system, we still go to the doctor’s office for a checkup. We may be sick or we may simply need a physical to look for warning signs that something could be wrong.
Your applications and networks need regular check-ups as well. These can be in the form of manual penetration tests or red team exercises. Penetration tests allow professionals from outside your company check your network and applications out for weaknesses and vulnerabilities. Red teams can be internal employees that are trained to look at your systems with an adversarial mindset. Both of these testing methods encourage deep thinking about how to break your systems and what would happen if an adversary gained access.
It is silly to not go to the doctor for fear that he my find something wrong. The problem exists whether it is diagnosed or not. Going to the doctor is what starts the healing process. A caring professional can help you to fix whatever problem is found. Similarly, using penetration tests and red team exercises may uncover some unpleasant vulnerabilities. Instead of feeling embarrassed, feel grateful. Once professionals uncover the problems, they can be resolved and you can have more confidence in your systems.
Match Your Analogy with Reality
The security industry is changing constantly. New threats and attacks are being introduced every day. Defenses are created for them, followed by different attacks. This cycle continues on and on.
The true picture of security is not that all invaders are stopped by a solid wall. Networks and Applications are like walls of a cell, resistant to unwanted traffic while allowing traffic necessary for business functions through the wall.
Security shouldn’t be assumed, it should be proactive.
-
Utilize threat hunting and automated detection systems to find intruders before they do any real damage
-
Feed what you learn back into automated tools to provide better detection in the future
-
Consider RASP tools to help protect your applications in real time
-
Use feedback from penetration tests and red teams to regularly check-up on your network or applications
Match your analogy with reality. Your network is not a fortress with a stone wall. It is a body, a cell, with defenses and strategies to find and repel invaders.
Good hunting!